What is DORA?
With DORA, Regulation (EU) 2022/2554 on digital operational resilience in the financial sector (Digital Operational Resilience Act), the European Commission is pursuing the goal of creating a uniform framework for the effective and comprehensive management of cybersecurity and ICT risks in the financial markets.
Table of Contents
DORA is “lex specialis” to the NIS-2 Directive, Directive (EU) 2022/2555 on measures for a high common level of cybersecurity across the Union (Network and Information Security Directive) and tightens cybersecurity requirements across the EU for banks and financial market infrastructures. As a result of DORA, the focus of financial supervision is shifting away from ensuring the financial resilience of financial companies towards ensuring the maintenance of resilient ICT operations in the event of a serious business interruption that could jeopardize the security of the network and information systems.
In parallel to DORA, regulatory technical standards (RTS) and implementation standards (ITS) will also be published to further specify the requirements of DORA. The first package of these RTS/ITS has already been published on 17.01.2024, the second package is in draft form and is due to be published on 17.07.2024.
In terms of content, DORA can be divided into 5 main areas:
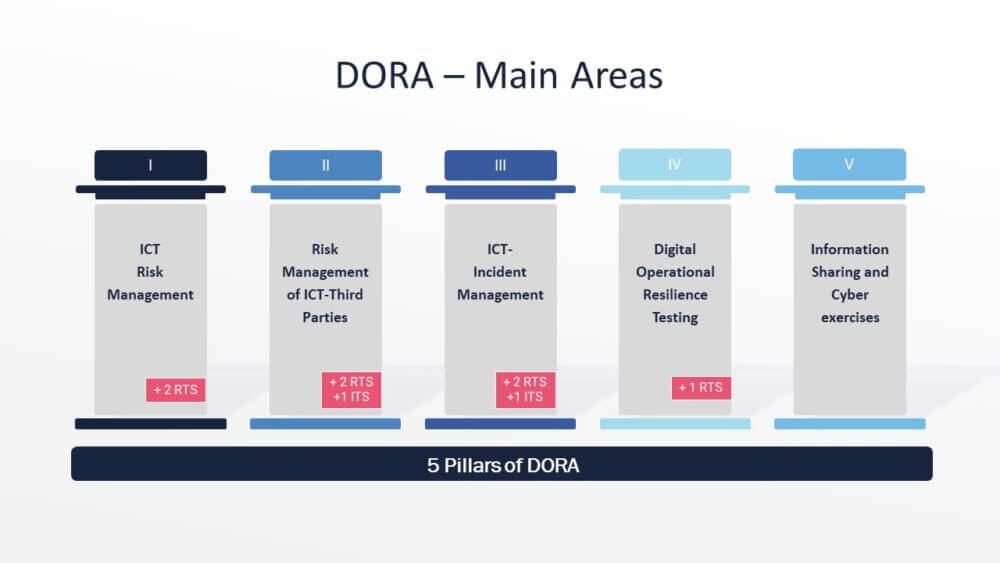
1. ICT risk management
DORA provides financial companies with harmonized and EU-wide requirements for ICT risk management. New and stricter, but also for the first time concrete requirements are placed on ICT governance and organization, on the ICT risk management framework, on ICT systems, protocols and applications and on further developments of ICT systems as well as on learning processes. These requirements are intended to help maintain or, if necessary, restore the functionality of financial companies, particularly with regard to cyber risks.
2. Management of ICT third-party risks
DORA requires financial companies to assess and monitor ICT third-party risks – throughout the entire life cycle of the purchase. An important prerequisite for this is that a risk analysis and due diligence is carried out before the contract is concluded. In addition, DORA specifies the minimum requirements that apply to the content of contracts with ICT third parties and that all ICT contractual relationships must be entered in an information register (similar to the outsourcing register). The information register must be submitted to the supervisory authority on request.
3. ICT incident reporting
DORA contains the obligation to implement a management process which, in addition to handling ICT-related incidents, also includes the monitoring, logging, classification and, if necessary, reporting of ICT-related incidents.
4. Testing digital operational resilience
With DORA, financial companies must constantly monitor and test their information and communication technology by establishing a risk-based, proportional testing program. Such a test program should, for example, analyze open source software, check network security and physical security in financial companies and include gap analyses, scenario-based tests, compatibility tests and penetration tests. In this way, financial companies should recognize, among other things, how prepared they are for ICT incidents and where they may have weaknesses in their digital operational resilience.
5. Information exchanges and cyber exercises
To strengthen the digital operational resilience of the European financial sector, DORA encourages financial firms to share information and intelligence on cyber threats. Financial undertakings must notify the competent supervisory authority as soon as their participation in such information sharing agreements has been confirmed or ends.
BaFin and the Deutsche Bundesbank are already preparing for DORA and are working on adapting their supervisory and administrative practices and implementing IT processes and systems within the framework of DORA. In future, BaFin will become the national reporting hub for ICT incidents in the financial sector. Furthermore, BaFin will receive notifications within the scope of ICT third-party management, which institutions and companies are obliged to do, and analyze them with regard to potential risks for the financial sector.
When does DORA apply?
- Entry into force: 01.2023
- Implementation deadline: 2 years, i.e. until 01.2025
DORA applies directly from 17.01.2025 and affects all supervised institutions and companies in the European financial sector and their IT outsourcing service providers
Who does DORA apply to?
DORA applies – with a few exceptions – in principle to all regulated financial companies in the EU and in particular also to ICT third-party service providers.
Compared to the two EBA guidelines on the management of ICT and security risks and EBA guidelines on outsourcing, DORA includes an even larger number and additional types of financial companies in its scope of application (see Art. 2 (1) DORA), among others:
- Credit institutions / banks
- Payment institutions,
- Insurances
- Investment firms,
- Trading venues/trading repositories
- crypto-asset service providers,
- credit rating agencies,
- crowdfunding service providers
- ICT third-party service providers
(The definition of “ICT third-party service providers” in Art. 3 No. 21 DORA includes providers of cloud computing services, software, PSPs data analysis services and data centers for financial companies as well as providers of core banking systems.)
What impact does DORA have on financial companies?
Despite the implementation deadline of 17.01.2025, there is already strong pressure on financial companies to identify and implement the need for action arising from the DORA requirements. As there is no transitional period, the requirements must be implemented by the deadline of 17.01.2025. The focus will be on the implementation of a comprehensive ICT risk management including various ICT policies, procedures and tools to identify risks, protect ICT systems and mitigate the risk of cyber security incidents, detect anomalous activity, recover from adverse events and use backup and other recovery methods.
DORA once again emphasizes that the overall responsibility for ICT risk management lies with the management, as only the management has the overall business overview and can make appropriate decisions. Due to the constantly changing cyber threat situation, financial companies must stabilize their ICT systems through regular updates, proactively manage vulnerabilities and take preventive measures in accordance with the requirements of the DORA. In the event of damage, sophisticated business continuity and recovery strategies as well as regular employee training are required.
A second focus of DORA is the requirement to regularly test their own operational resilience. Testing should be risk-based rather than standardized – financial institutions are expected to test the risks that are most relevant to their investment services and business lines. This is to ensure that firms’ cyber risk controls are tailored to their particular business.
In addition, financial companies must ensure the analysis, classification and documentation of ICT-related incidents and their reporting to the competent supervisory authority (similar to the notification pursuant to Section 54 ZAG).
DORA also requires assessing the risks associated with third-party services and having policies in place to ensure that only appropriate third-party services are used. As the financial sector increasingly relies on large technology providers for their ICT infrastructure and cloud services, mainly using the largest global firms, there are increasing ICT concentration risks that need to be identified and addressed by financial companies at an early stage.
DORA also specifies the minimum contractual clauses that outsourcing contracts must contain, distinguishing between non-critical and critical (essential) ICT services.
As part of risk management, financial companies are obliged to keep a register of information about all outsourced ICT services. DORA sets out specific requirements for the format and content of this register, which have been defined in a separate Technical Implementation Standard. In addition, outsourcing, especially to third countries, requires careful due diligence.
DORA requires the internal organizational structure to be adapted by setting up new functions. While the internal control system previously included a risk controlling function, a compliance function and an information security officer, DORA requires the establishment of a new independent control function for the management and monitoring of specific ICT risk. This “ICT risk management function” must be separate from other control functions and internal audit.
In addition, pursuant to Art. 5 para. 3 DORA, a function for monitoring contracts for the use of ICT services must be set up or a member of management must be appointed for this purpose. This function should be congruent with the Outsourcing Officer already specified in BAIT/ZAIT.
Furthermore, a crisis management function must be set up that is responsible, among other things, for defining procedures for handling internal and external crisis communication when activating ICT business continuity plans or response/recovery plans.
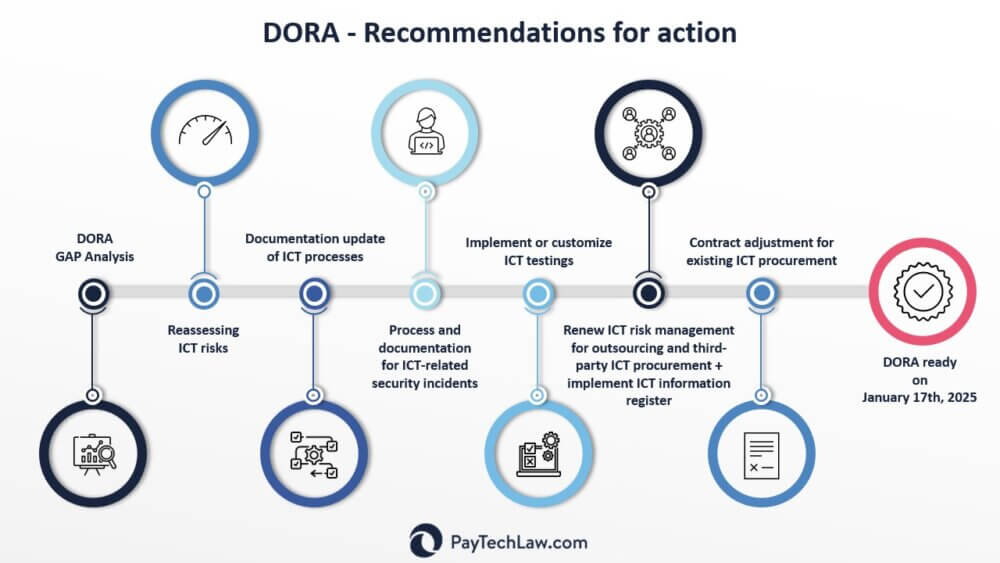
Recommendations for action
In view of the approaching implementation deadline of January 17, 2025, financial companies should start assessing the implications of DORA and implementing the DORA requirements immediately. DORA specifies the existing regulations and standards on the ICT requirements of financial companies and expands them to an extent that, depending on the type of financial company and the degree of maturity achieved so far in implementing the current regulatory requirements for ICT, triggers a considerable need for implementation. Financial companies are therefore urged to review the DORA requirements now, carry out corresponding GAP analyses in their company and implement the extensive changes.
All ICT risks must be re-evaluated and integrated into the overall risk management system of institutions. The definition of a comprehensible, non-overlapping risk taxonomy/methodology adapted to the risk distribution of an institution is critical to success, so that, for example, the allocation, management and responsibility for information and outsourcing risks or cyber risks are clearly defined.
The technical regulatory and implementation standards for DORA (DORA-RTS/DORA-ITS), some of which are still in draft form, already make it clear that a considerable amount of additional work is required to document ICT processes and ICT systems, particularly in the area of ICT risk management. For example, more than 20 different internal ICT-related guidelines are required (including on ICT asset management, encryption and cryptographic controls, capacity and performance management, data and system security, logging, network security, change management, access monitoring, monitoring of ICT systems, management of ICT-related security incidents, ICT-related business continuity in the event of a crisis and testing of various emergency plans, as well as testing of ICT systems) are required with DORA-RTS on the ICT risk management framework (Art. 15 DORA).
In addition, according to Art. 17ff. DORA, financial organizations must develop a process for handling ICT-related incidents in order to identify and mitigate these and significant cyber threats. Serious ICT-related incidents (these are ICT incidents that have a significant adverse impact on the network and information systems that support critical or important functions of the financial undertaking) must be reported to BaFin and, where appropriate, to those affected.
DORA focuses increasingly on the prevention of IT and cyber threats and therefore provides specific guidelines for testing digital operational resilience, which must be implemented as an integral part of ICT risk management. This requires adjustments or new implementations of testing processes and the corresponding documentation. Although the BAIT/ZAIT already provide for regular or event-driven reviews of the security of IT systems, e.g. through penetration tests, DORA specifies the requirements for such tests and tightens them through the dedicated requirement of threat-led penetration tests (TLPT).
While there is some overlap between DORA and the provisions of the EBA guidelines on outsourcing, the rules are not fully consistent and DORA introduces some new minimum requirements for outsourcing agreements. Due to this divergence, financial firms cannot assume that an outsourcing arrangement that complies with the EBA rules will automatically ensure compliance with DORA. Companies should therefore compare their current contracts with ICT service providers with the requirements of DORA and take steps to ensure that any gaps identified are closed before the end of the implementation period. DORA makes no exception for existing ICT contracts, so these must be adapted and renegotiated. In order to take into account all minimum contents according to DORA in a legally secure manner when adapting IT service contracts, professional/technical understanding of the service outsourced to third parties, experience with existing EBA/BaFin regulations and legal know-how are required. Ongoing regulatory initiatives should already take into account the new requirements in the DORA-relevant areas in order to create synergies. As DORA does not differentiate between outsourcing and other procurement of ICT services (but between non-critical and critical/essential ICT functions), the minimum requirements for ICT contracts from DORA may also have to include contractual relationships that are not included in the current outsourcing register. The new ICT information register must be introduced (similarly and in parallel to the outsourcing register) with all its content and format requirements and must be kept up to date from 17.01.2025.